
Transform your Products without compromising
Cyber Security
to reduce business risks

While digital transformation presents multiple opportunities for your business, your expanding digital presence also brings accompanying cyber security risks that can adversely impact your business.
Cyber-attacks can compromise your applications, devices and data, and cause immense losses. Once hackers gain access to one of your systems, they can move through your network and attack other assets. They can disrupt critical activities, and compromise the operations, security and privacy of your business and your customers.
As you implement your digital transformation strategy, all your products, services and systems need to be developed without compromising security. They need to be constantly tracked for vulnerabilities, and should have protection that restrict access. Your business needs to be alert and protect your assets to reduce business risks from cyber security breaches.
But a constantly evolving threat landscape poses several complexities and challenges that compromise cyber security:
The increased digital footprint of your applications, data and processes offers more potential entry points. In addition, a combination of private, on-premises networks and cloud networks results in connections through the publicly-accessible Internet.

Rapidly changing digital technology increases the risk of introducing new security vulnerabilities. Simultaneously, criminals are also continuously innovating new ways of hacking.

In addition to using new techniques, hacking is also becoming sophisticated. Using AI and other technology advancements, criminals can launch attacks that are difficult to detect.
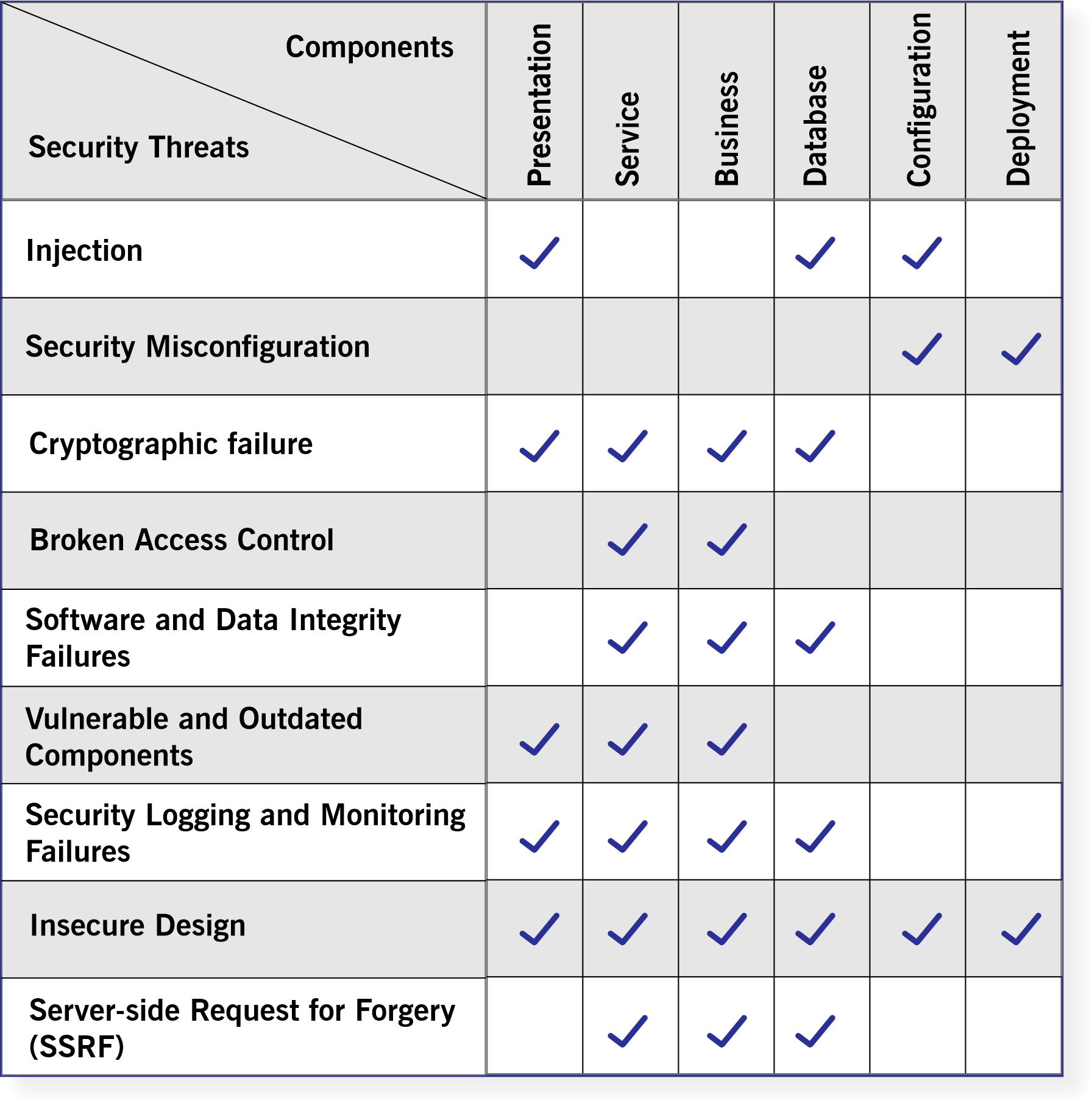
Most attacks occur due to flawed coding, such as a failure to sanitize inputs and outputs. Different cyber security threats target different components.
To arrest such threats, security aspects have to be addressed throughout the product development life-cycle, not just in the final testing and deployment phases. Special attention is required in the design and coding phases of product development to ensure that cyber security aspects are not compromised.
Do you have an effective security strategy for your products and services?
Connect with us today to protect your offerings with modern security technologies.
Cyber security mechanisms that have been typically used include threat modelling, static code analysis and runtime vulnerability assessment. However, the impact of digital transformation on products and services is also driving changes in cyber security approaches. Some of the recent trends in cyber security include:


Security is being integrated into every device to provide a critical security layer. Manufacturers are adopting a privacy-by-design framework, in which privacy is the key design element. Digital certificates and public key infrastructure (PKI’s) are being used to enable a more secure onboarding process.

With the explosive growth in data and increased security threats, business are re-evaluating their data security governance to incorporate best cyber security practices. Data security governance is also being expanded to address governance of technologies such as big data and cloud.

Cyber security automation is bringing in efficiencies in incident detection, attack analysis and response. Not only does it eliminate the risk of human errors, it is also helping in the automatic remediation of security issues. For e.g., a robust, automated digital immune system protects applications & services from anomalies, such as the effects of software bugs or security issues by making applications more resilient so that they recover quickly from failures. It can reduce business continuity risks created when critical applications & services are severely compromised or stop working altogether.

Traditional passwords that have been used for verification and identification, are giving way to more secure authentication alternatives such as biometric verification, voice recognition, two-factor authentication, etc. to guarantee data security. New methods such as Identity-as-a-service (IDaaS) are becoming popular and eliminating the need for passwords. New technologies such as Blockchain are also enabling the verification and authentication of users and devices with robust, transparent protocols and public key cryptography.
Are you facing challenges in implementing security for your products and services?
Connect with us today to leverage our security expertise.
At Celstream, with nearly two decades of experience in delivering product engineering services for diverse and complex products and apps, we understand what it takes to implement cyber security for your hardware and software products and applications, as you realize your digital transformation strategy.
Our product engineering services teams have considerable experience working on diverse aspects of hardware, software and data security. Over the years, we have built a comprehensive knowledge base of cyber security best practices, checklists and test cases for design, coding, testing and operations.

We are an ISO 27001:2013 certified company. Our teams follow secure software development lifecycle (SDLC) principles in projects for our customers. We use tools, both free and licensed, to gauge the security level of products. We write scripts for various security tools, execute the workflows, generate reports, and analyze the results to improve the security of products. We can configure network and computing infrastructure – Firewalls, HTTP Proxies, Virus protection, OS patches, etc. – for mitigating security issues.
Celstream’s standard practice of ensuring cyber security involves these eight steps:
While exploring security requirements, it is crucial to consider capturing the entire gamut of requirements. We achieve this by looking at how the end-users and the external systems interact with the product and identify the vulnerability points.
Threat modelling is a structured activity for identifying and evaluating product threats and vulnerabilities. It enables us to identify, quantify, and address the security risks associated with the product.
This is a live document which serves as a ready reckoner for our developers on security best practices. It is prepared in the form of a checklist and updated regularly to incorporate learnings from security incidents in the project and outside.
Our DevSecOps practices include security design reviews, scanning code for security vulnerabilities, and remediating bugs that present legitimate threats. By introducing security earlier in the SDLC, we ensure that security is considered seriously rather than treating it as an afterthought.
Increasingly applications are now built using pre-built open source and commercial libraries and services. Special care is taken to ensure that these external components meet the security expectation of the product under consideration.
This involves writing test cases for security requirements. Besides executing these product-specific test cases, we use penetration tools in a proxy configuration that allows network traffic to pass through and do ethical hacking to penetrate deep into the product and report the results.
Secure deployment or the IT security policy ensures that the deployment environment is safeguarded from different kinds of external threats. This includes configuring firewalls, maintaining the environment up-to-date on security patches, implementing access control and security policy, etc.
On a regular basis, we release security patches for the deployment setup, third-party and open source libraries and the core product itself to contain any new threats.
Our product engineering services teams have expertise in the following security tools:
TRANSFORM YOUR
PRODUCTS AND SERVICES TODAY!